
Don’t Wait for a Breach—Schedule Your Free Security Review

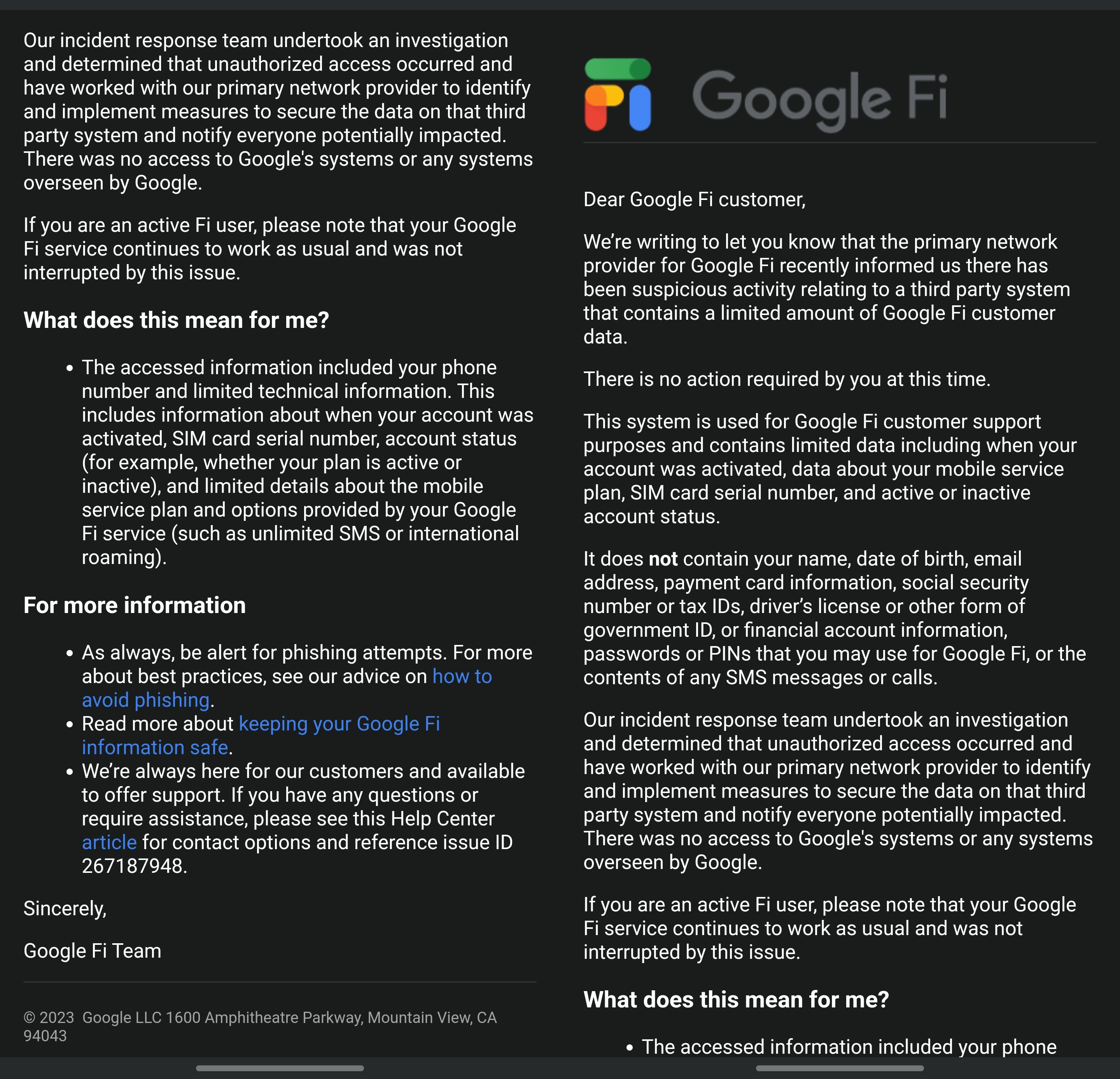
Google Fi, a US mobile service provider, recently disclosed a data breach that impacted a limited number of its customers. The company sent notifications to its affected customers informing them that their phone numbers, SIM card serial numbers, account status, account activation date, and mobile service plan details were accessed by hackers.
However, Google has reassured its customers that sensitive information such as full names, email addresses, payment card information, social security numbers, tax IDs, government IDs, account passwords, and contents of SMS and phone calls were not part of the breached systems.
Source: Twitter @Dmite09
The data breach comes after T-Mobile, one of Google Fi’s parent tower companies for service, suffered a massive data breach affecting 37 million customers.
T-Mobile revealed at the end of January that an API flaw was exploited, which resulted in hackers gaining access to customer’s account data, including name, billing address, email, phone number, date of birth, T-Mobile account number, and information about the number of lines on the account and plan features.
However, not all Google Fi customers received the same information.
“Additionally, on January 1, 2023 for about 1 hour 48 minutes, your mobile phone service was transferred from your SIM card to another SIM card. During the time of this temporary transfer, the unauthorized access could have involved the use of your phone number to send and receive phone calls and text messages. Despite the SIM transfer, your voicemail could not have been accessed. We have restored Google Fi service to your SIM card.” Came the notice from Google Fi to the customer.
The customer reported on Reddit that they received multiple unauthorized access and password reset notifications. These notifications came from their email addresses, outlook accounts, crypto wallet accounts, and even Authy – a token authentication app. The alleged access to Authy was allowed to an internal setting of Authy which allowed multiple devices to access the app, a setting that needs manually turned off by customers.
The customer recounted watching “in real time” their accounts being hacked and stolen, including banking accounts. Worse, the customer only knew this was happening because of email alerts as the SMS authentication alerts were not being sent to their phone. This was because the hacker had stolen access to their SIM and phone number. Within minutes, the hackers had access to their two-factor authentication codes, Authy token authentication app, and more.
“The hacker used this to take over three of my online accounts — my primary email, a financial account, and the Authy authenticator app, all because they were able to receive my SMSes and therefore defeat SMS-based 2-fac,”
SIM Swapping is a form of social engineering in which a cyber criminal impersonates you to your mobile carrier and convinces them to transfer your phone number to a mobile SIM card that they control. Once the number is ported, the attacker has access to your text messages, including MFA codes, and can then use that information to breach your online accounts or take over services secured by your phone number.
Once the number is ported, the threat actors would have access to the victim’s text messages, including multi-factor authentication codes, which could be used to breach online accounts or take over services secured by the person’s phone number.
Currently, cyberanalysts are researching this breach and believe that Google Fi’s access could be related to the T-Mobile breach due to T-Mobile being one of the parent tower service companies for Google Fi’s service.
The data breaches at T-Mobile are not new, with the company suffering multiple data breaches since 2018.
2019 – 3% of all T-Mobile customers data was breached.
2020 – Prepaid customers’ data & T-Mobile employees’ email accounts breached.
2020 – Customer information (phone numbers, call records) breached.
2021 – Internal T-Mobile application breached.
2021 – Hackers brute-forced their way through T-Mobile’s network
2022 – Lapsus$ extortion gang breached network with stolen credentials.
How to Protect Yourself from SIM Swapping.
We at Motiva Networks can help you plan and see if your data has been compromised with a Free Confidential Cybersecurity Risk Assessment. Or you can schedule a quick 10-minute call to discuss the best options for your Agency or small business, or go over any questions you might have HERE.
