
Don’t Wait for a Breach—Schedule Your Free Security Review

As cybercrime continues to evolve, so too do the tactics used by hackers. In recent years, an increasing number of companies have turned to cyber insurance as a means of protecting their businesses. However, this has led to a shift in the way that hackers target their victims.
The strain of malware named HardBit was introduced in October of 2022 according to BleepingComputer. The newest upgrade, 2.0, was detected in November 2022 according to a report from data security company, Varonis.
HardBit 2.0 is able to modify victims Registry on their devices to disable Windows Defender’s real-time monitoring process among other protections.
It’s malware that digs into computer systems and finds sensitive information. Once sensitive information is found it encrypts them and deletes the Volume Shadow copies to make data recovery extremely difficult. It overwrites the original files themselves with encrypted data which makes it much more difficult for experts to recover versus other strains of malware.
HardBit 2.0 ransomware targets specific details including the victim’s username and computer or device names, installed hardware such as CPU, hard drives, and graphics cards, network settings including IP configuration and MAC addresses, as well as system manufacturer and version from the BIOS and motherboard, and time zone and location information.
Once the ransomware is activated, the victim has 48 hours to contact the hacker over an open-source encrypted peer-to-peer communications app. Once in contact, the hackers behind HardBit 2.0 try to confirm whether or not the victim has cyber insurance.
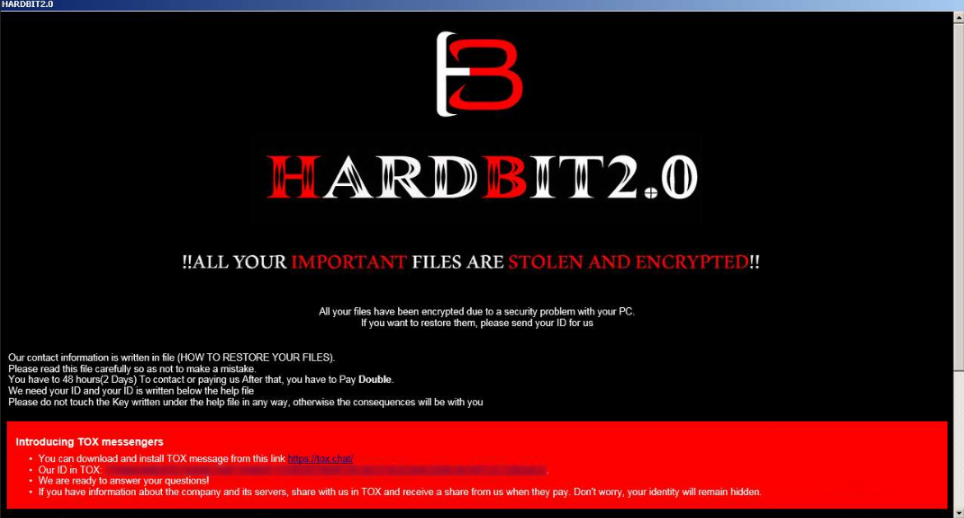
Source Varonis
Hackers attempt to convince the victim that sharing insurance details will be beneficial in getting their files back. The hackers make it seem that the insurance company is the one to blame, making the victim more willing to share confidential information. By providing insurance information to the hackers, they are able to ensure that their payment demands are at the top limit of the payout scale, and also is within coverage.
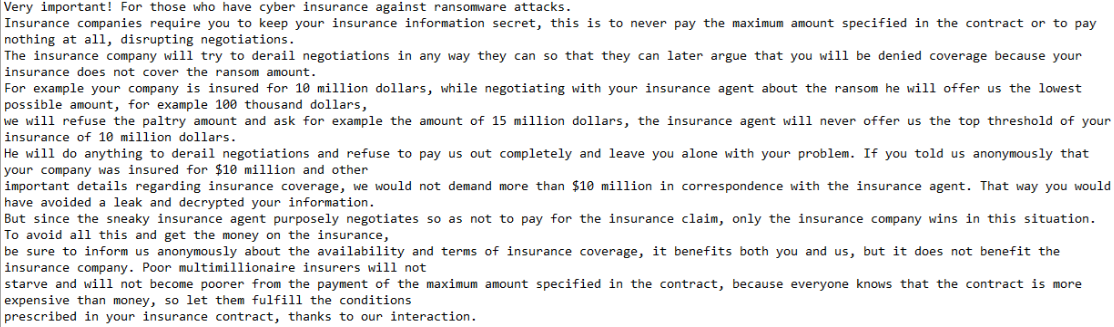
Image Source Varonis
“To avoid all this and get the money on the insurance, be sure to inform us anonymously about the availability and terms of the insurance coverage, it benefits both you and us, but it does not benefit the insurance company,” HardBit hackers say.
By providing insurance information to the hackers, they are able to ensure that their payment demands are at the top limit of the payout scale, and also is within coverage.
Further, they gain confidential insurance information of the victim that they could use later against the victim again or against the insurance provider company.
“Once a cybercriminal finds a formula that works for them, they’re going to stick to it,” said Tyler Moore, a cyber security professor at the University of Tulsa to SecurityWeek.
Of course, paying the ransom does not always equal getting your files back and so it is highly encouraged to refuse any ransom payments and report the issue to law enforcement as soon as possible.
How does the HardBit 2.0 Ransomware Work?
The full report from Varonis provides in-depth technical details on how HardBit 2.0 functions.
Raising Concerns
Cybersecurity experts have raised concerns since 2019 about cyber insurance payouts fueling ransomware attacks and demands. This has led cybersecurity insurers to increase their premiums and mandate stricter cybersecurity controls and implementation to be eligible for policies.
As reported by SecurityWeek, the FBI states that more than 1,400 ransomware instances were reported last year. Reported payouts from victims totaled over $3.6 million. However, officials believe this is only a fraction of the true amount as many victims choose not to report the incidents due to fear of loss of trust and damage to their company’s reputation.
Josephine Wolff, professor of cybersecurity policy at Tufts University comments that “[when you say], ‘Oh, this is just something my insurance covers,’ victims are forgetting that they are contributing direct financial resources to future criminal operations.”
Companies should consider the consequences of cyber insurance payouts and balance them with the costs of implementing proper cybersecurity measures to prevent such attacks from occurring in the first place.
Protect yourself from ransomware:
Full HardBit 2.0 Ransomware Note:
HARDBIT RANSOMWARE
what happened?
All your files have been stolen and then encrypted. But don’t worry, everything is safe and will be returned to you.
How can I get my files back?
You have to pay us to get the files back. We don’t have bank or paypal accounts, you only have to pay us via Bitcoin.
How can I buy bitcoins?
You can buy bitcoins from all reputable sites in the world and send them to us. Just search how to buy bitcoins on the internet. Our suggestion is these sites.
hxxps://www.binance.com/enhxxps://www.coinbase.com/hxxps://localbitcoins.com/hxxps://www.bybit.com/en-US/<<
What is your guarantee to restore files?
Its just a business. We absolutely do not care about you and your deals, except getting benefits. If we do not do our work and liabilities – nobody will cooperate with us. Its not in our interests.
To check the ability of returning files, you can send to us any 2 files with SIMPLE extensions(jpg,xls,doc, etc… not databases!) and low sizes(max 1 mb), we will decrypt them and send back to you.
That is our guarantee.
How to contact with you?
Or contact us by email:>>godgood55@tutanota.comalexgod5566@xyzmailpro.com<;<
How will the payment process be after payment?
After payment, we will send you the decryption tool along with the guide and we will be with you until the last file is decrypted.
What happens if I don’t pay you?
If you don’t pay us, you will never have access to your files because the private key is only in our hands. This transaction is not important to us,
but it is important to you, because not only do you not have access to your files, but you also lose time. And the more time passes, the more you will lose and
If you do not pay the ransom, we will attack your company again in the future.
What are your recommendations?
– Never work with intermediary companies, because they charge more money from you. For example, if we ask you for 50,000 dollars, they will tell you 55,000 dollars. Don’t be afraid of us, just call us.
Very important! For those who have cyber insurance against ransomware attacks.
Insurance companies require you to keep your insurance information secret, this is to never pay the maximum amount specified in the contract or to pay nothing at all, disrupting negotiations.
The insurance company will try to derail negotiations in any way they can so that they can later argue that you will be denied coverage because your insurance does not cover the ransom amount.
For example your company is insured for 10 million dollars, while negotiating with your insurance agent about the ransom he will offer us the lowest possible amount, for example 100 thousand dollars,
we will refuse the paltry amount and ask for example the amount of 15 million dollars, the insurance agent will never offer us the top threshold of your insurance of 10 million dollars.
He will do anything to derail negotiations and refuse to pay us out completely and leave you alone with your problem. If you told us anonymously that your company was insured for $10 million and other
important details regarding insurance coverage, we would not demand more than $10 million in correspondence with the insurance agent. That way you would have avoided a leak and decrypted your information.
But since the sneaky insurance agent purposely negotiates so as not to pay for the insurance claim, only the insurance company wins in this situation. To avoid all this and get the money on the insurance,
be sure to inform us anonymously about the availability and terms of insurance coverage, it benefits both you and us, but it does not benefit the insurance company. Poor multimillionaire insurers will not
starve and will not become poorer from the payment of the maximum amount specified in the contract, because everyone knows that the contract is more expensive than money, so let them fulfill the conditions prescribed in your insurance contract, thanks to our interaction.
Your ID :-
Your Key –
With over 25 years of experience, we at Motiva Networks can help you plan and see if your data has been compromised with a Free Confidential Cybersecurity Risk Assessment. Or you can schedule a quick 10-minute call to discuss the best options for your Agency or small business, or go over any questions you might have HERE.
