
Don’t Wait for a Breach—Schedule Your Free Security Review

Hacker group Luna Moth investing in call centers to extort ransom payments from victims
Luna Moth, a ransomware group active since March of this year – also known as the Silent Ransom Group – has been utilizing multiple tactics to extort ransom from victims.
In a new report from Palo Alto Networks Inc.’s Unit 42 – read here -, the group has been identified as the source of the new rise of call centers in ransomware attacks.
Luna Moth previously has used tactics such as phishing campaigns, fake subscription renewals, and more. The new tactic of using call centers allows them to target and tailor their ransom methods to each individual victim, making their chances of success much higher.
Victims are tricked first by legitimate and trusted system management tools that interact with their computers that are typically not detected as malicious, therefore bypassing typical basic security.
The group then sends phishing emails or notices that the victim’s payment methods – such as a credit card or bank account – has been charged for an amount usually under $1,000. The email itself is legitimate, contains no malware, is personalized to the victim, and was sent from a legitimate email service, the report from Palo Alto Networks Inc. details.
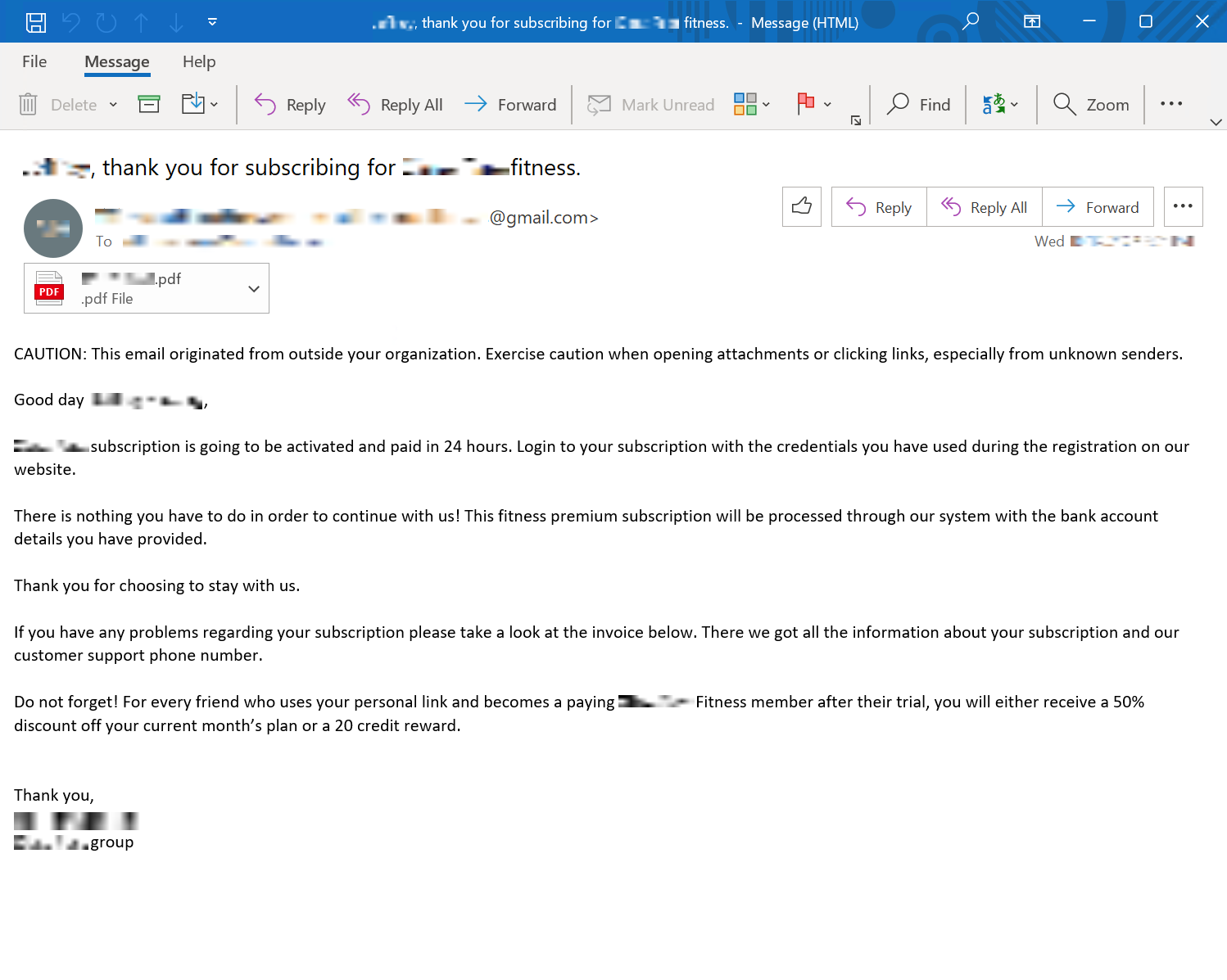
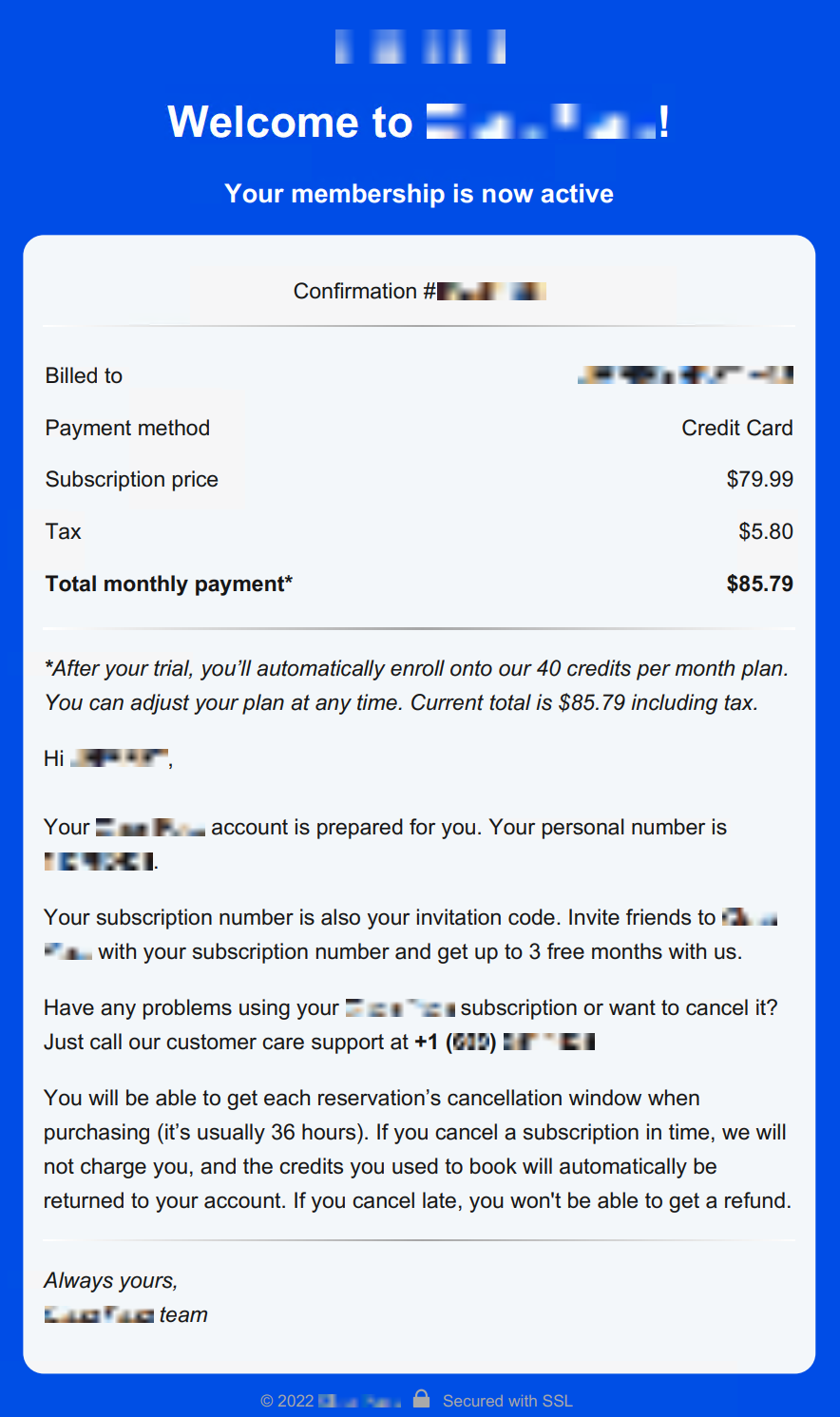
Inside of the receipt, the victim finds a service phone number or email they can contact about this charge. That number routes the victim directly to a Luna Moth call center and a live hacker agent.
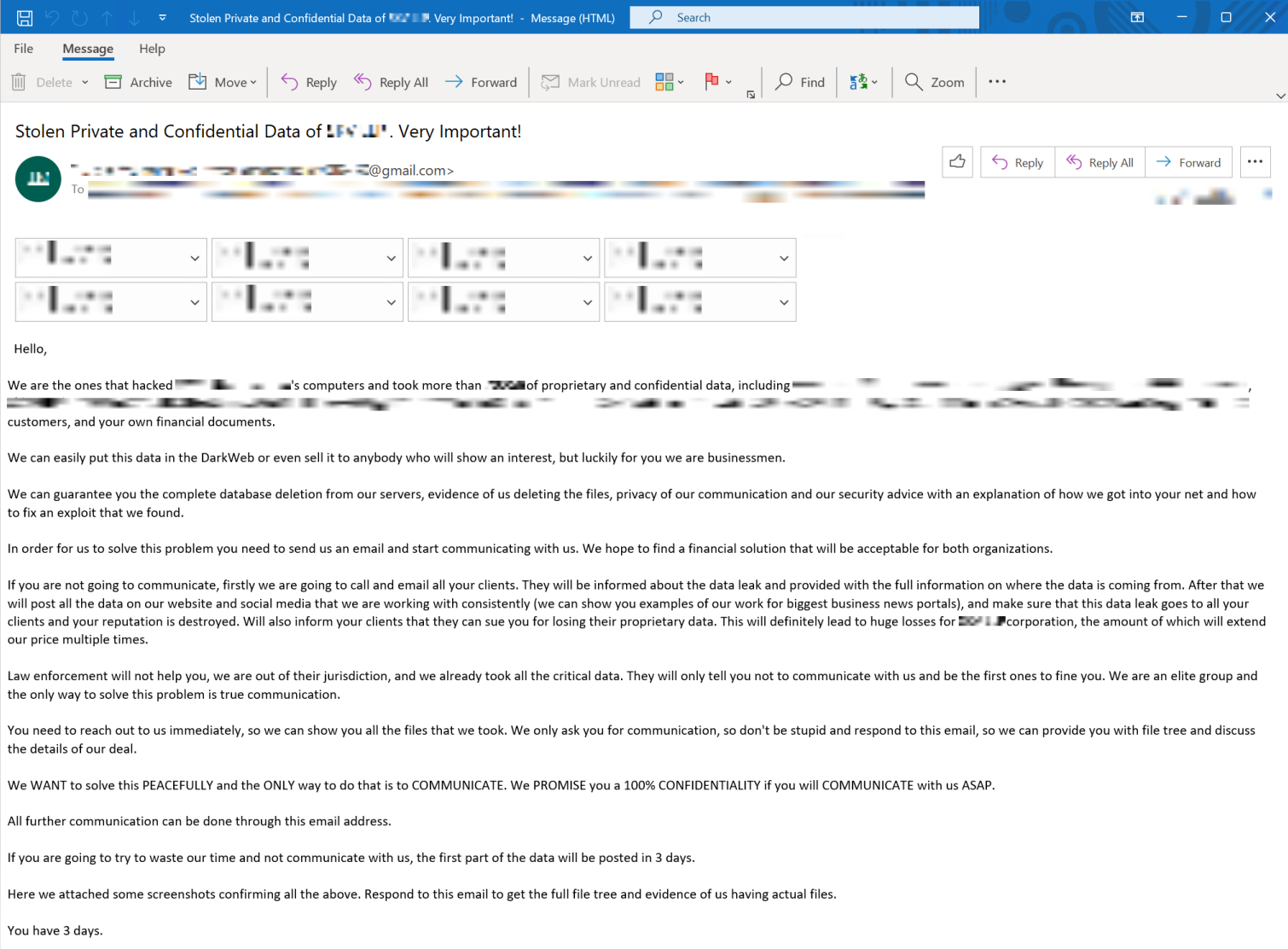
From there, the live hacking agent will talk to victims and extort more information from them under the guise of being legitimate.
“In this way, the threat actor is able to compromise organizational assets through a social engineering attack on an individual. After the data is stolen, the attacker sends an extortion email demanding victims pay a fee or else the attacker will release the stolen information.” Palo Alto Networks Inc. researchers say. “If the victim does not establish contact with the attackers, they will follow up with more aggressive demands. Ultimately, attackers will threaten to contact victims’ customers and clients identified through the stolen data, to increase the pressure to comply.”
Because of the nature of this type of attack, cyberanalysts warn that they are extremely difficult to detect.
“Employee cybersecurity awareness training is the first line of defense.”
Cybersecurity awareness training is a must for all in this day and age of overwhelming ransomware attacks. Other steps such as multi-factor authentication, security programs, device monitoring, and more are extremely important and necessary to be implemented for all devices that access the internet, access personal data, or have access to such.
“Unit 42 expects callback phishing attacks to increase in popularity due to the low per-target cost, low risk of detection and fast monetization. While groups that can establish infrastructure to handle inbound calls and identify sensitive data for exfiltration are likely to dominate the threat landscape initially, a low barrier to entry makes it probable that more threat actors will enter the fray.”
Worried your current or lack thereof of cybersecurity practices that may be putting you at risk? Click here to schedule a brief 10-minute call to discuss your situation, needs and concerns. If appropriate, we can conduct a simple security assessment for free to know for sure if your network and data is safe or call us at 646-374-1820.
