In a recent sophisticated phishing campaign, hackers capitalized on a zero-day vulnerability in Salesforce’s email services, targeting precious Facebook accounts.
Breaking It Down
Guardio Labs, a cybersecurity research firm, detected an issue labeled “PhishForce.” In simple terms, this allowed bad actors to send deceptive emails through Salesforce, bypassing its usual safety checks. Moreover, they combined this flaw with a loophole in Facebook’s gaming platform, enhancing the chances of their hack succeeding.
The tactic is akin to a wolf in sheep’s clothing: using Salesforce—a platform we associate with credibility—to send potentially harmful emails. This strategy cleverly sidesteps most standard email security measures, placing these questionable emails directly in recipients’ primary inboxes.
The Mechanics of the Attack
In business lingo, we often hear of Salesforce’s “Email-to-Case” feature. It’s a tool many companies use to transform customer queries into actionable items. Here’s a simplified breakdown of the hackers’ strategy:
- They tapped into this "Email-to-Case" system to secure a Salesforce-specific email address.
- Created an inbound email under the trusted "salesforce.com" banner.
- Designated this as the main sending address for large email batches.
- Sealed the deal by verifying they "owned" this domain.
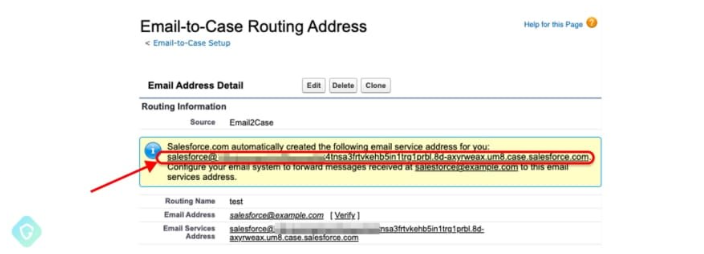
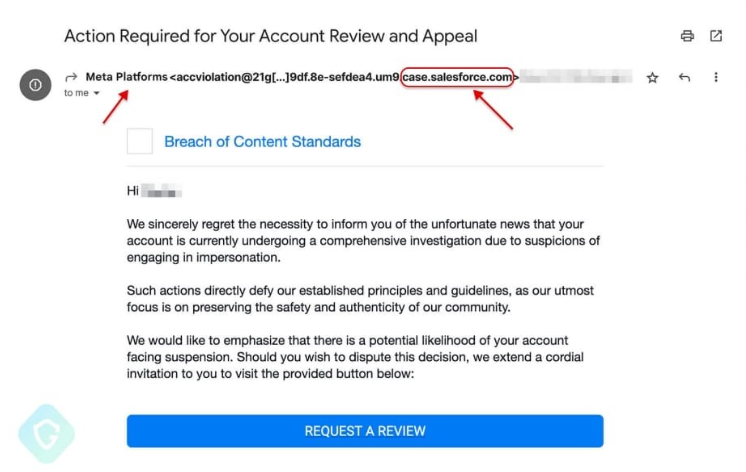
(Image Sources Guardio Labs)
In essence, these cybercriminals wore a Salesforce mask, allowing them to send emails that bypassed regular checks and balances.
The Aftermath and Resolution
Upon discovering this, Guardio Labs immediately alerted Salesforce in late June 2023. By the end of July 2023, Salesforce had acknowledged and rectified the problem.
A perplexing aspect was the misuse of a retired Facebook platform, “apps.facebook.com.” While this platform was officially retired in 2020, older accounts with previous access privileges could still utilize it. It’s speculated that hackers might be obtaining these older accounts through covert channels.
What Does This Mean for You?
For CEOs overseeing businesses that utilize Salesforce, this event may raise eyebrows among your clientele and partners. If they begin questioning the authenticity of emails from Salesforce, it could introduce wrinkles in your daily operations. Furthermore, the notion of trusted platforms being exploited could increase the probability of innocent engagements with harmful content. This incident is yet another major reminder of the critical need for robust cybersecurity measures to protect your operations and maintain client trust.
Steps for Enhanced Safety
In this digital era, a proactive stance is invaluable. Here are some easy-to-follow guidelines:
- Stay Alert: If an email seems off, it's best to double-check. Avoid clicking on unfamiliar links or downloading attachments from unsolicited emails.
- Be Direct: If in doubt, manually enter the website's address or reach out to the sender using a previously known method.
- Bolster Security: Implement multi-factor authentication (MFA) where available. Think of it as an additional password step, further locking out intruders.
- Educate: Regularly remind your teams about the perils of phishing and encourage open communication about suspicious emails.
- Stay Updated: Ensure your systems are updated with the latest antivirus and security tools.
Secure your network today with a FREE risk assessment from our expert team. Let us help you safeguard your client’s sensitive data and prepare effectively against cyber threats before they happen. Give me a call at 646-374-1820 or email me at walter@motiva.net



