On Friday Sept 16th, Uber confirmed that it had been victim of a major cyber security breach. Uber revealed that the hack was completed by an 18 year old, who gained internal access to databases and systems. The teen used social engineering to trick an employee into giving up confidential information.
According to news reports, Uber had received the message “I announce I am a hacker and Uber has suffered a data breach.” The hacker used text messages to another Uber worker claiming that they worked for the company and needed tech access to systems, which the Uber employee provided password access after being spam messaged for over an hour. The teen then infiltrated Uber systems, including their Slack message system where they posted memes and spam messages to clog up communications. Employees as well faced harassment to include attempting to log into Uber’s website and being met with pornographic images.
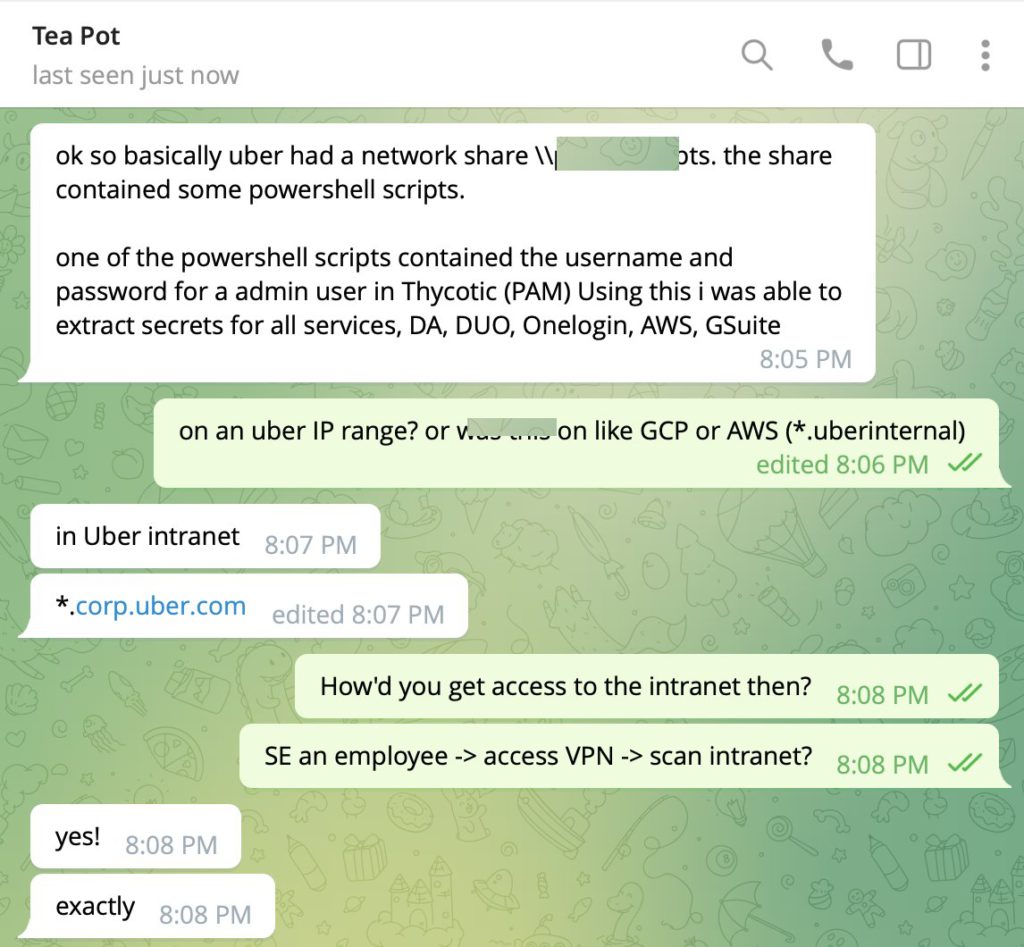
The 18 year old hacker also was able to find unencrypted admin passwords within the servers, and use these passwords to take over Uber completely. They gained access to the security emergency accounts as well, effectively taking them offline and unable to respond to the cybersecurity emergency.
Lapsus$, a major hacking group, confirmed that they were part of the attack. This group has previously attacked Microsoft, Okta Inc., and Nvidia. The 18 year old hacker also breached Rockstar Games systems this week and leaked confidential gameplay footage of an upcoming unreleased game. Cybersecurity Experts say that if you’ve ever had your data within the Uber app, you are potentially compromised.
HackerOne is currently aiding Uber in locking down systems and attempting to restore the breach. “We’re in close contact with Uber’s security team, have locked their data down, and will continue to assist with their investigation,” Chief Hacking Officer of HackerOne, Chris Evans, told BBC news.
Uber had a massive lack of network security and seemingly allowed employees to have greater access to confidential systems and resources than they were supposed to have access to. Admin credentials as well not being encrypted and instead able to be found in plain text scripts hosted on network shares proves again that Uber was not operating under proper cybersecurity guidelines. Further, it was seemingly easy to get around MFA/2FA (2-Factor Authentication) by purely spamming an employee until they accepted the request, a show of failure of proper employee training against cyber criminal attacks.
Uber claims that their systems were largely unaffected by the breach despite all coming to light. The matter is currently being investigated by the U.S. Department of Justice and the F.B.I. Uber has been in the news before for a prior hack in 2016, in which hackers were able to steal names, email addresses and phone numbers of 50 million Uber users worldwide, including driver’s licence numbers of 7 million drivers in the US. Uber was forced to pay the hackers ransom and also attempted to cover up the breach. In July 2022, Uber officially came forward with a statement on the breach. They had to pay $212 million in damages for the incident in civil litigation charges.
“The Uber breach highlights both the power and downsides of centralization. An employee account was compromised by being overwhelmed by Push Auth Notifications of Multi-Factor Authentication. This led to a PowerShell script getting discovered, with admin credentials to their Thycotic PAM (Privileged Access Management) tool. With all credentials being part of this PAM solution, now the entire org was compromised because the PAM had access to AWS, Google Workspace, Slack, and more. Often, even with best-in-class budgets or security tools, it comes down to compromising an employee with high privileges.” -Abhay Bhargav – CEO AppSecEngineer
Don’t fall victim to a data breach or cybersecurity risk. We at Motiva Networks can help you make a plan and see if your data has been compromised with a Free Confidential Cybersecurity Risk Assessment.






